Investigating of Cyber-Crime with OSINT
Mon, 02 Sep 2024

Follow the stories of academics and their research expeditions
???? Don’t be the Next Victim! Learn How to Shield Yourself Against the Silent Threat of SIM Swap Scams ????
In the vast digital realm where convenience and vulnerability coexist, there’s a lurking menace that
has swindled countless individuals out of their identities, savings, and peace of mind – the insidious SIM swap scam.
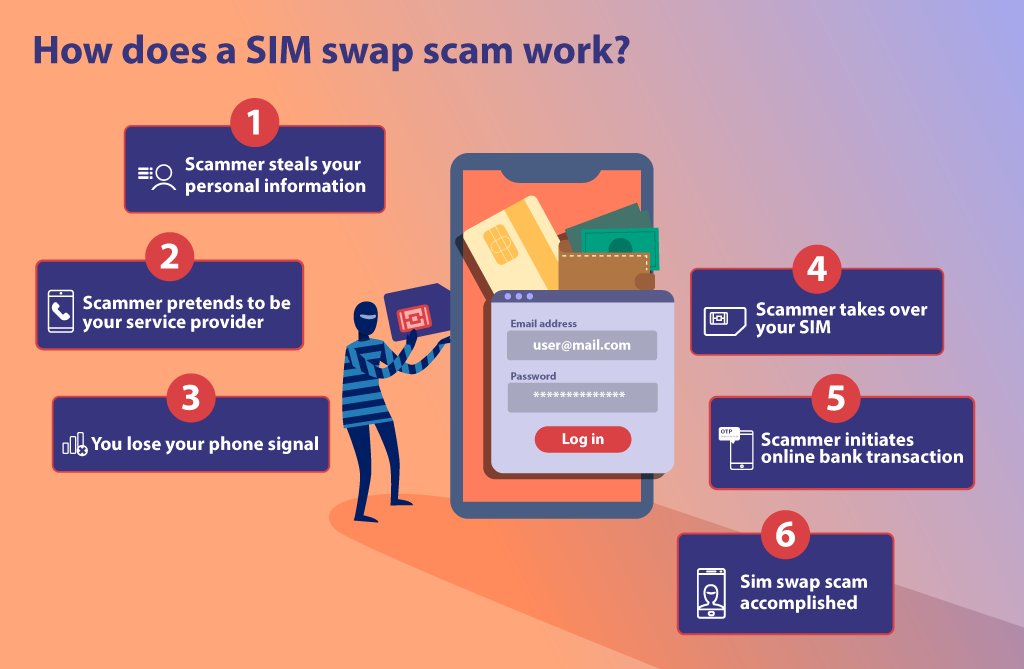
In this comprehensive guide, we delve deep into the world of SIM swap scams, shedding light on what they are,
how they work, and, most importantly, equipping you with the knowledge to protect yourself.

A SIM swap scam, short for Subscriber Identity Module swap scam, is a meticulously orchestrated act of fraud
in which cybercriminals wrest control of your phone number. The perpetrators leverage this hijacked number
to gain unauthorized access to your calls, text messages, and, most alarmingly, your two-factor authentication (2FA) codes.

To understand how a SIM swap scam unfolds, it’s crucial to break down its components:

Now that we’ve unveiled the sinister workings of SIM swap scams, it’s time to arm ourselves with the knowledge and defenses necessary to thwart these audacious attacks. Consider implementing the following strategies:
As we navigate the treacherous waters of our digital era, it’s imperative to stay one step ahead of cybercriminals who relentlessly devise new tactics. Furthermore, the SIM swap scam is just one manifestation of this ongoing struggle for security and privacy.
By adopting the countermeasures outlined in this guide, you can significantly reduce your vulnerability to SIM swap scams. Knowledge, vigilance, and proactive security measures will fortify your digital defenses.

Protect yourself today, and ensure a safer, more secure digital tomorrow. Cybercriminals thrive on our ignorance; let’s deny them that advantage.
In an interconnected world where convenience and vulnerability coexist, the threat of SIM swap scams looms large. However, this comprehensive guide has not only provided you with a thorough understanding of what SIM swap scams are but also delved into how they work and, most importantly, how to protect yourself against them.
Remember, knowledge is your most potent weapon in the ongoing battle against cyber threats. Stay informed, stay vigilant, and share this information with your friends and family to create a safer online environment for everyone.
If you found this detailed guide valuable, don’t keep it to yourself. Share it with your friends, family, and colleagues to empower them with the knowledge needed to protect themselves in the digital age. Together, we can build a robust defense against SIM swap scams and ensure a safer digital future for all. Knowledge is power; let’s wield it wisely.
Mon, 02 Sep 2024

Mon, 02 Sep 2024

Mon, 26 Aug 2024

Leave a comment